During Cybersecurity Awareness Month, we’re here to share some tips around building a strong cybersecurity culture at your company. While we are not cybersecurity experts, we do hear from our large customer base that they experience these types of scam attempts regularly. When looking for specific advice, the first place to start is your own security team or other trusted cybersecurity experts for their recommendations — they know security and your environment best.
As a finance professional, you’re both the primary target and the last line of defense when it comes to fraud and scams. How you react to fraud attempts can directly impact your bottom line.
Here’s what you’re up against:
Social engineering
This fraud comes in many forms and involves a fraudster tricking an employee into providing sensitive information or access. Fraudsters typically spend time gathering information before they attack so they can be as convincing as possible, and gain the trust of their target. Finally they attack, using tactics like creating urgency or using emotional appeals to get what they want.
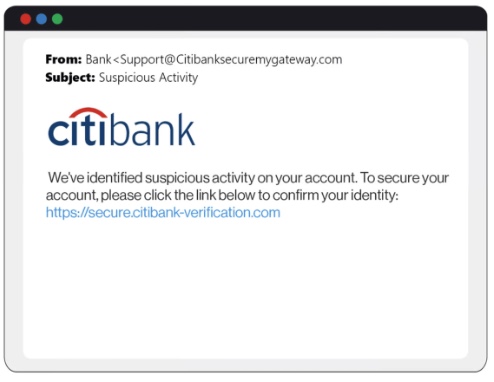
An example of a phishing email, via KeepNet1.
Business Email Compromise
Though email is an essential communication tool, it’s highly susceptible to scams. Business email compromise (BEC) happens when fraudsters attempt to access a company’s systems or steal information or money by impersonating a trusted person, like an executive. When these attacks are successful, fraudsters enter a company’s network undetected, where they can request fraudulent transfers, steal credentials, and access confidential information.
Vendor impersonation and payment redirection
Fraudsters often exploit our sense of routine — 60% of BEC-related fraud attempts cited vendor impersonation as a tactic. Fraudsters will pose as trusted vendors to redirect payments from the accounts payable team to fraudulent accounts, all while creating a false sense of urgency. This type of scam comes in the form of phishing emails, fake invoices, and compromised email accounts.
Invoice fraud
With the prevalence of AI, unfortunately creating fake invoices (or manipulating real ones) has never been easier. Fraudsters create these fake invoices for goods or services never received, or by modifying real invoices to inflate charges, changing the recipient details, or committing card fraud. In this scheme, bad actors take advantage of gaps in an organization’s verification processes, counting on the business to approve the payment without thorough scrutiny to verify the vendor’s information.
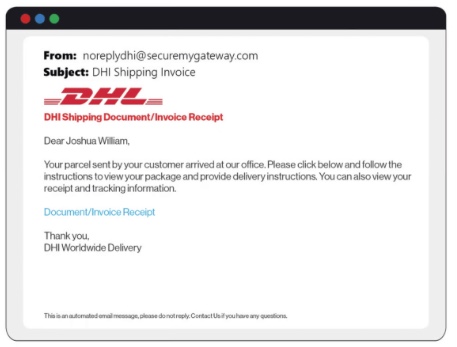
An example of invoice fraud, via KeepNet2
Employee fraud
Employee fraud can look like skimming sales, receivables, or refunds, and setting up billing schemes like shell companies or using company funds for personal purchases. It also includes check tampering, including forging endorsements or altering payees. Unfortunately this type of fraud is not limited to large enterprises. According to CompareCamp, a business with an employee count of less than 100 typically loses around $200,000 while those with over 100 employees only report a smaller median loss of $104,000.
What to watch for
With a little common sense and diligence, your team can avoid many of these scams.
When it comes to emails and overall communication, keep an eye out for urgent language and pressure to pay now, or well before the due date. Fraudsters prey on our sense of routine, and when that routine changes, sometimes we panic.
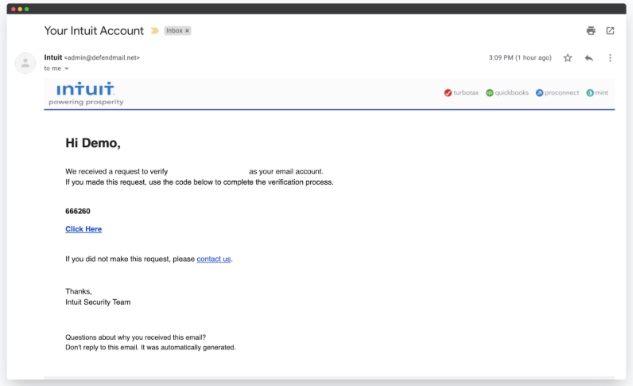
A common phishing email, via Hook Security3
Look for slight variations in email addresses, such as extra periods or letters, or domains that just don’t make sense like the example above.
Here are a few other suspicious behaviors to watch for:
- New vendors requesting immediate payment
- Invoices with incomplete or suspicious contact information
- Round-number amounts or unusual invoice formats
- Reluctance to provide additional documentation
- Avoiding phone conversations
- Requests to keep changes “confidential”
As a finance team and at your overall organization, strengthening your current security framework is a great place to start. People, process, and technology can work together to create checks and balances, and stronger overall security controls that aid in prevention. This can look like:
- Collecting comprehensive verification before making any bank account changes, or when onboarding a new vendor.
- Documenting all change requests and approval processes to maintain a strong audit trail.
- Calling your main vendor contact using previously verified phone numbers prior to making any account changes.
- Limiting access to account systems based on role, need-to-know and the least privileges necessary.
- Implementing multi-factor authentication (MFA) standards if not already in place
- Scheduling regular team training sessions
- Establishing clear incident response protocols
Keep in mind that MineralTree can help keep your team running efficiently. Here’s how we can help:
- Controlled vendor creation/alteration: Vendors can only be created directly in your ERP, reducing exposure to fraudulent vendor setups and you can decide who at your org can edit vendor data within MineralTree. In addition, MineralTree can notify all users any time vendor records are updated in MineralTree (i.e. if a payment account is changed).
- Approval workflows: Tiered invoice and payment approvals along with separation of duties ensure no single user can approve a payment or invoice without review.
- Invoice-level controls: Exceptions, duplicate detection, and configurable thresholds highlight suspicious invoices before payment.
- Audit trails: Full visibility into invoice submission, approvals, and payment history supports quick detection of anomalies.
Visit our resource center for the MineralTree team’s latest insights!




